
Sorry, my teammates. I audited you guys using CloudTrail.
Let's monitor AWS IAM users' activity!
Audit AWS IAM Users
You can use this small project to audit your AWS IAM users to prevent unexpected behavior and charge.
If you follow the steps below, you can make a small system that notifies you when an IAM user uses not only AWS console but also API call using SDK.
How to use
Notification channel - Slack
First of all, you need a channel to receive an alert message through it. My favorites are Slack and Telegram and I'm going to use Slack in this example.
- Log in Slack and go to here to create new app.
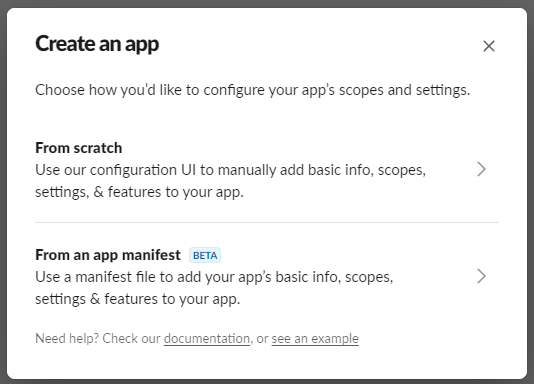
- Click Create New App button and select to create from scratch.
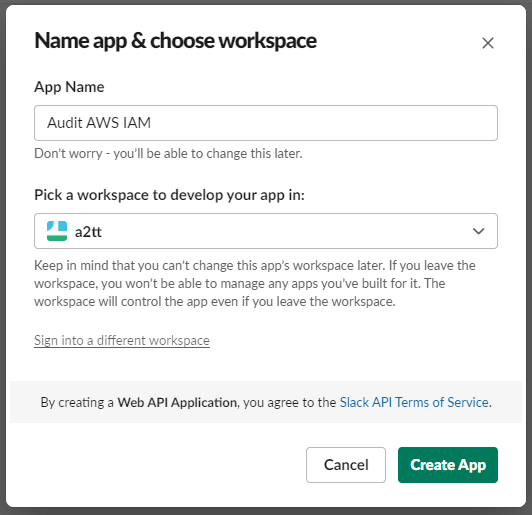
- Enter the name of your app and pick a workspace where your app can work.
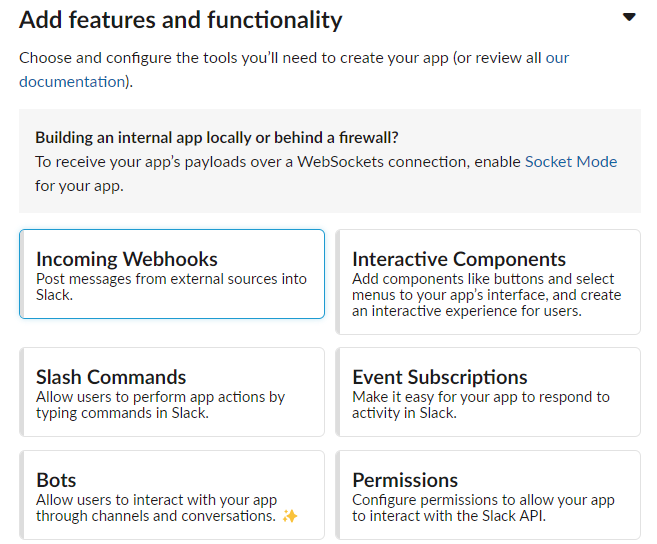
- Now, you are in the configuration page. Let's configure Incoming Webhooks. Click this button.
- Activate incoming webhooks.
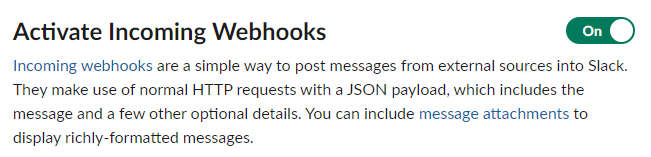
- Click Add New Webhook to Workspace and choose a channel that audit messages will be posted on.
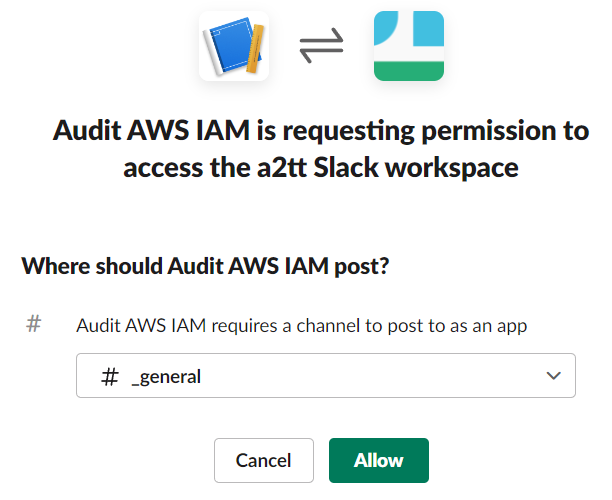
- Then, you have created new webhook URL. When sending JSON data to the URL, that data will be posted on the selected channel.
AWS CloudTrail
You can use AWS CloudTrail to track user activity and API usage.
- Log in AWS account that has a permission for CloudTrail and for CloudWatch.
- Go to CloudTrail dashboard and click Create trail.
- Fill in the required fields and make sure you enable CloudWatch Logs. Then, press next button.
- Choose log event types you want to record and configure for them, and finish creating trail.
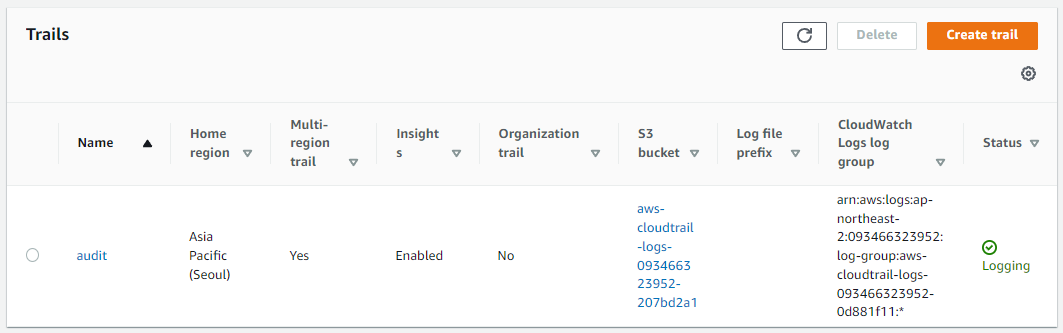
Now, all events are logged with CloudWatch.
AWS Lambda
Although CloudTrail tracks and records events, it does not send any message by itself.
You need to process and filter logs, and send message to your slack channel. We are going to use AWS Lambda for this.
-
Log in AWS account that has a permission to create AWS Lambda, and go to the page of AWS Lambda.
-
Click Create function.
-
Fill in the required form, select runtime as Python 3.9 or newer, and then create it.
Now, your function is created. Let's upload code that will be used to process CloudTrail logs. -
Download this repository or git clone it.
$ git clone https://github.com/a2tt/Audit-AWS-IAM-User.git -
Copy
configs.example.pytoconfigs.pyand modify it with yours. -
Archive this directory by executing shell script.
Make sure you have installed python3 on your machine.
$ . zip_function.shWhat this script does is ...
- Make directory named 'package'.
- Install python packages required into the directory.
- Zip python code with the packages.
-
Click Upload from - .zip file to upload
function.zipto AWS Lambda.
AWS CloudWatch
Finally, you need to configure AWS CloudWatch to trigger the Lambda function.
We are going to use Subscription filters functionality.
-
Log in AWS account that has a permission for CloudWatch and go to CloudWatch - log groups menu.
-
Find your cloudtrail log groups, and click the group.
-
Click Subscription filters tab and press Create - Create Lambda subscription filter.
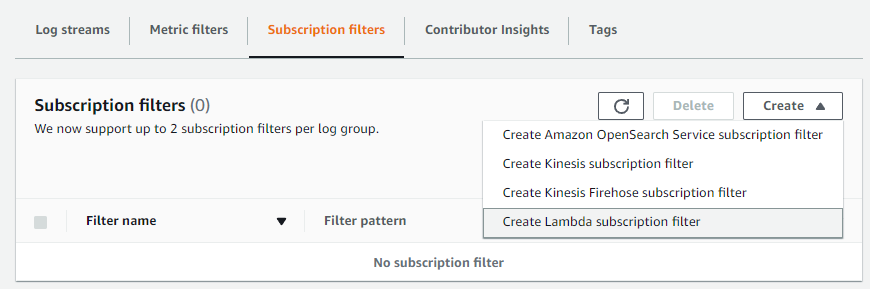
-
Select your Lambda function and set log format as Amazon CloudTrail.
-
This step is one of the most important and can be changed for your taste.
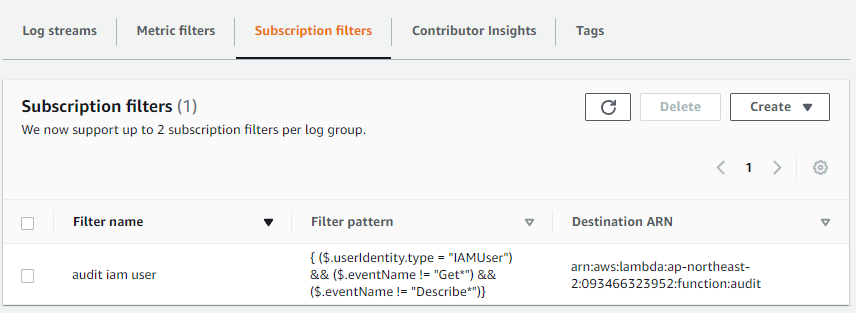
You can set Subscription filter pattern to filter out unwanted events triggering the Lambda. I'm using this rule:{ ($.userIdentity.type = "IAMUser") && ($.eventName != "Get*") && ($.eventName != "Describe*") }By filtering "IAMUser", it will trigger Lambda for the logs related to the events triggered by IAM user,
and by filtering out "Get*" and "Describe*", you won't receive the rampant and frequent messages that are not likely to be important.You can check out what patterns are allowed here.
-
It's time to start streaming!
Result
When you log in as an IAM user, roam about AWS console, do API call using SDK(e.g. boto3) or do API call with AWS CLI, you will receive a message about it.
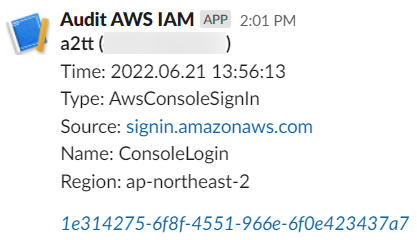
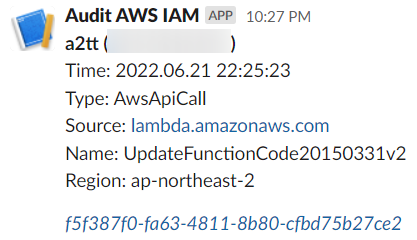
Conclusion
You should know that well defined Role-based Access Control using IAM is more important than auditing.
Nonetheless, you can use this simple system for tracking users in a small sized group.